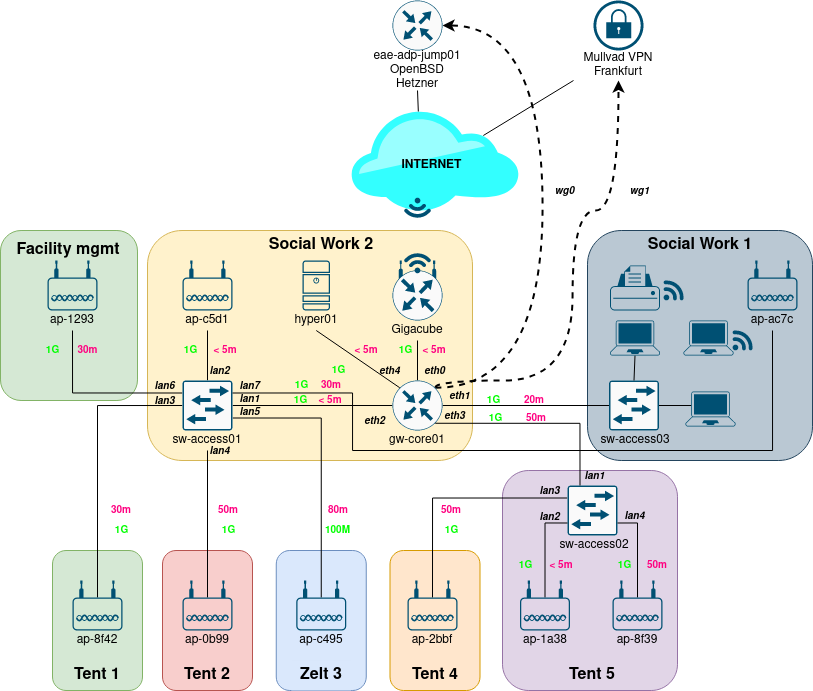
5.6 KiB
System/Network Overview
Diagram:
IPAM / Device Overview:
| Name | Location | MGMT IPv4 | MAC | Device | Notes |
|---|---|---|---|---|---|
gigacube-2001 |
Büro | 192.168.0.1 |
c8:ea:f8:b6:e9:50 |
ZTE MF289F/Gigacube | property of Saxonia Catering/rental from Vodafone |
gw-core01 |
Büro | 10.84.1.1 |
00:1a:8c:48:b3:98 |
Sophos SG125r2 | |
sw-access01 |
Büro | 10.84.1.11 |
bc:cf:4f:e3:bb:8d |
Zyxel GS1800-8HP | |
sw-access02 |
Zelt 5 | 10.84.1.12 |
bc:cf:4f:e3:ac:39 |
Zyxel GS1800-8HP | |
sw-access03 |
Sozialarbeit | / | / | KTI KGS-510F | manageable but used as a dumb switch |
hyper01 |
Büro | 10.84.1.21 |
00:23:24:54:f0:fe |
Lenovo ThinkCentre ? | |
monitoring01 |
hyper01 |
10.84.1.51 |
16:b9:13:c3:10:5e |
Proxmox Container | |
mon-e2e-clients01 |
hyper01 |
10.84.7.30 |
ca:ac:5a:d0:b6:02 |
Proxmox Container | used for end to end monitoring of the public net |
ap-2bbf |
Zelt 4 | 10.84.1.30 |
24:de:c6:cc:2b:bf |
Aruba AP-105 | |
ap-1a38 |
Zelt 5 | 10.84.1.35 |
18:64:72:cf:1a:38 |
Aruba AP-105 | |
ap-ac7c |
Sozialarbeit | 10.84.1.31 |
24:de:c6:c3:ac:7c |
Aruba AP-105 | |
ap-0b99 |
Zelt 2 | 10.84.1.32 |
6c:f3:7f:c9:0b:99 |
Aruba AP-105 | |
ap-c5d1 |
Büro | 10.84.1.33 |
ac:a3:1e:cf:c5:d1 |
Aruba AP-105 | |
ap-c495 |
Zelt 3 | 10.84.1.34 |
ac:a3:1e:cf:c4:95 |
Aruba AP-105 | |
ap-8f42 |
Zelt 1 | 10.84.1.36 |
d8:c7:c8:c2:8f:42 |
Aruba AP-105 | |
ap-8f39 |
Zelt 5 | 10.84.1.37 |
??:??:??:??:??:?? |
Aruba AP-105 |
Upstream Connectivity:
The gigacube itself only get's an RFC1918 address from Vodafone (CGNAT - no IPv6).
Our gateway (gw-core01) itself also nats, because there is no way to configure additional networks on the gigacube.
Currently the generated traffic is directly routed into the internet - without an vpn tunnel.
Therefore v4 streams get masqueraded 3 times.
Cloud VMs:
| VM Name | IPv4 | IPv6 | Location | Provider | Type | Description | Notes |
|---|---|---|---|---|---|---|---|
eae-adp-jump01 |
162.55.53.85 |
2a01:4f8:c0c:1281::/64 |
Germany - Nuerenberg - DC3 | Hetzner | CX11 | vpn and jump host for remote access | kvm access: @hirnpfirsich |
Networks:
| Name | VLAN | v4 Space | v6 Space | Description |
|---|---|---|---|---|
mgmt |
1 | 10.84.1.0/24 |
/ | default network which is used for administrative and monitoring tasks |
clients |
2 | 10.84.4.0/22 |
/ | this is where the wifi clients live |
wan |
3 | 192.168.0.0/24 |
/ | created by the gigacube. wan for our gateway |
backbone |
/ | 10.84.254.0/30 |
/ | tunnel network between gw-core01 and eae-adp-jump01 |
backoffice |
8 | 10.84.8.0/24 |
/ | backoffice network for the orga |
WiFi Networks:
| SSID | Encryption | VLAN | Description |
|---|---|---|---|
GU Deutscher Platz |
/ | 2 | |
GU Deutscher Platz Backoffice |
wpa2 psk | 8 |
Remote Access / VPN:
Remote access is possible via a eae-adp-jump01.
gw-core01 digs a wireguard tunnel into eae-adp-jump01 (network: 10.54.254.0/30, wg port 51820).
This point-to-point link is used to establish an ospf adjacency between the two routers.
(gw-core01 uses frr as the routing daemon, eae-adp-jump01 uses openbsds own ospfd).
The most straight forward way to access machines inside the EAE is to use the ProxyJump feature of ssh.
Take a look at the README.md in the root of this repo for details.
In the future there maybe wg profiles for admins to directly route into the network.